If you suspect that WordPress has been hacked and you are not confident that you can fix it yourself, please contact me or your other contact person. WordPress Freelancer for a non-binding initial assessment.
Cleaning malware from websites often involves several steps and can only be carried out by very technically skilled people. For those who still want to try it themselves, this article is for you.

Signs that your WordPress site has been hacked
Detecting a hack on your WordPress website can be a challenge, especially if the signs are subtle. A clear warning sign is when you no longer have access to the WordPress admin panel.
This indicates that your login data may have been compromised. Changes to the design or content of your site that you have not authorized are also an indicator of unauthorized tampering. A sudden and unexplained drop in website traffic may indicate tampering that is affecting your SEO efforts.
You should also take note if your website unexpectedly redirects visitors or sends spam emails. Warning messages from browsers or security plugins that indicate a possible compromise should also be taken seriously. In addition, the appearance of new user accounts with admin rights that were created without your consent is a clear sign that WordPress has been hacked.
These warning signs should not be ignored as they indicate a breach of your website's security and require quick action.
Here is a summary of the signs of a WordPress hack:
- Inability to log in to the admin panel.
- Unauthorized content or design changes.
- Unexpected drop in traffic.
- Forwarding of website content and spam e-mails.
- Warnings from browsers or security plugins.
- Appearance of unknown users with admin rights.
Common causes of hacks on WordPress sites
There are many reasons why WordPress sites are targeted by hackers, but some causes are particularly common.
One of the main reasons is insecure passwords, which make it easier for hackers to gain access to your site. Many users tend to use simple or commonly known passwords such as "12345" or "password", which poses a significant security risk.

Another major problem is outdated software. Many WordPress site owners neglect to regularly update their WordPress version, plugins and themes. These updates often contain important security patches, and failing to update makes the site vulnerable to attacks.
Finally, the use of insecure code is a significant risk factor. This includes the use of plugins from untrusted sources or the installation of nulled plugins, which can often contain backdoors or malware. It is crucial to only use software from reliable sources and to carry out regular checks for potential security vulnerabilities.
How WordPress sites are hacked
Backdoors
A common way in which WordPress is hacked is through so-called backdoors or malicious code, which are exploited by script kiddies. These allow hackers to bypass normal authentication procedures and gain undetected access to website files. These backdoors are often embedded in scripts or hidden files, which makes them difficult to detect.
Brute force attacks
Brute force attacks are another common method where hackers use automated tools to guess passwords by trial and error. This is particularly effective for websites with weak passwords and can give hackers access to admin areas.
Cross-site scripting (XSS)
Cross-site scripting, often abbreviated as XSS, is an attack method in which hackers insert malicious scripts into a website. These scripts can then be passed on to unknowing users when they visit the affected site, allowing the hackers to steal sensitive information or perform other malicious actions.
SQL injection
In an SQL injection, hackers exploit vulnerabilities in the database query of a website. By injecting malicious code into SQL queries, they can access or manipulate sensitive data.
Malicious redirects and pharma hacks
Malicious redirects and pharma hacks are forms of attacks in which visitors to a hacked site are redirected to other, often harmful websites. In pharma hacks, the hacked site is manipulated so that it ranks for spam-related search terms, which can damage the site's reputation. Google often does not even notice that the site has been hacked or infected with malicious code.
Denial of Service (DoS)
DoS attacks aim to paralyze a website by overloading it with requests. This can happen when hackers exploit vulnerabilities in the code base of a website to flood it with requests and thus disrupt its operation.
Tips and immediate measures after a hack on your WordPress site
If you discover that your WordPress site has been hacked, quick action is crucial to limit the damage and restore security. Here are the most important steps you should take immediately:
Set website to maintenance mode
The first thing you should do is put your website into maintenance mode. This prevents visitors from accessing the potentially compromised page and protects them from potential security risks. It also preserves your brand image as visitors will not be exposed to content that has been hacked.
Reset passwords
An essential step is to reset all passwords. This includes the WordPress admin password, FTP access data, database passwords and the passwords of your hosting account. Strong, unique passwords are crucial here.
Update plugins and themes
Update all your plugins and themes. Outdated plugins are often gateways for hackers. Make sure you use the latest versions to close known security gaps.
Remove unknown users
Check the user list of your WordPress dashboard and remove all unknown or suspicious users, especially those with administrator rights.
Delete unwanted files
Remove all suspicious or unknown files from your website directory. Pay particular attention to recently added files that do not originate from you.
Clean sitemap
If your sitemap is affected by the hack, generate a new one and submit it to search engines like Google to ensure that your SEO ranking is not negatively impacted.
Reinstall WordPress core
In some cases, it may be necessary to reinstall the WordPress core files to ensure that no compromised files are left behind.
Clean up database
Clean your WordPress database of suspicious entries left by hackers. This can be done manually or with the help of specialized plugins.
It is important to proceed carefully with all these steps and, if in doubt, seek professional help to ensure that your website is completely cleansed of the hack and that there are no further security risks.
DIY guide to fixing a hack on your WordPress site
If you decide to fix a hack on your WordPress site yourself, you can find a detailed guide here. Please note that technical knowledge is required and, if in doubt, professional help should be sought.
1. backup of the website and database
Before you start the cleanup, back up your website and database. This is important in case errors occur during the cleaning process. Use your hosting backups or a backup plugin to create a complete copy of your website.
2. identification of the hack
Use online tools or a WordPress Malware Scanner to scan your website for malware and other malicious code. Check whether you can log in to the WordPress dashboard, whether your site has been marked as unsafe or whether there are unwanted redirects or links.
In most cases, the scanner finds unique patterns in files such as documented here on GitHub finds:
3. checking the core files
Perform an integrity check of the WordPress core files. Plugins such as Sucuri can help to identify modified or infected files.
4. check for recently changed files
Check your themes, plugins and the uploads directory for recently changed files. Suspicious files should be examined more closely.
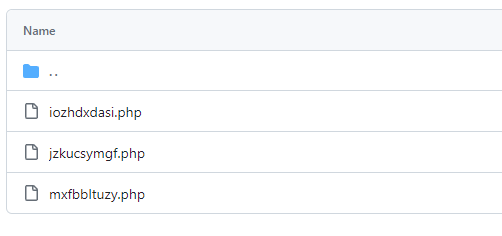
5. manual removal of the malware infection
Replace infected core files with fresh copies of WordPress.org. Be careful not to overwrite the wp-content directory and the wp-config.php file. For custom files, you should use your most recent backups.
6. cleanup of the hacked database tables
Search your database for suspicious entries and remove them manually. Use your database management tool to do this.
7. backing up user accounts
Check the user accounts in your WordPress dashboard and delete all unknown accounts. Make sure that you are the only user with admin rights.
8. removal of hidden backdoors
Search for files that could serve as backdoors. These are often disguised and difficult to recognize.
9. updating WordPress and resetting the settings
Update WordPress, all plugins to the latest versions. Also reset all configuration settings, including user passwords and secret keys.
10. installation of security plugins
Install security plugins such as MalCare, WordFence or Sucuri to protect your website and prevent future attacks.
11. creating backups
Set up a reliable backup routine to ensure regular backups of your website.
12. checking the local computer
Scan your local computer for malware to make sure there are no security threats such as keyloggers.
13. use of a firewall plugin
Install a firewall plugin to protect your website from external threats.
14. removal of malware warnings
After you have cleaned up your website, request a check with search engines and security services to remove any blacklist entries.
These steps provide a comprehensive guide to fixing a hack on a WordPress site. Remember that fixing a hack can be complex and professional help should be sought if in doubt.
Prevention of future hacks on your WordPress site
To prevent future hacks of your WordPress site, it's important to take proactive security measures. Here are some key strategies you can employ:
Use secure passwords
Make sure that all passwords associated with your website - including your WordPress admin password, FTP access, and your database - are strong and unique. Use a combination of letters, numbers and special characters and change your passwords regularly.

Update website regularly
Always keep your WordPress installation and all plugins up to date. Many updates contain security patches that fix known vulnerabilities.
Use of secure plugins and themes
Only install plugins from trustworthy sources such as the official WordPress directory. Avoid using nulled plugins or themes, as these often contain insecure code.
Clean up WordPress installation
Remove inactive plugins and themes, as these can represent a potential security vulnerability. Also delete all unnecessary files and database tables.
Install SSL certificate
An SSL certificate encrypts the data transmitted between the user's browser and your website, thereby improving security.
Choose high-quality hosting
Avoid cheap hosting providers as they often have overcrowded servers and less robust security measures. A quality hosting provider can offer proactive security measures and support in the event of a hack.
Set up firewall
Use a firewall to prevent unauthorized access and increase the security of your website. Many security plugins offer integrated firewall functions.
Two-factor authentication
Introduce two-factor authentication for the WordPress login. This provides an additional layer of security, as a second form of proof (e.g. a code on a cell phone) is required for access.
Regular safety checks
Carry out regular security checks to ensure that your website is free of malware and vulnerabilities. Use special security plugins or services to do this.
Education and awareness
Stay informed about the latest security trends and threats and, if necessary, train your team or users on cybersecurity basics.
By applying these measures, you can significantly increase the security of your WordPress site and minimize the risk of future hacks.
Conclusion: the most important steps if your WordPress site has been hacked
Facing a hack of your WordPress site can be a scary experience, but it's important to know that there are effective steps you can take to repair the damage and restore security. Early detection of signs of a hack, such as unauthorized changes to content or unexplained user behavior changes, is crucial for a quick response. In the event of a hack, it is important to proceed systematically: Put your site in maintenance mode, change all passwords, check and clean your website of malware, and update all system components.
However, it is even more important to take preventative measures to avoid future hacks. These include using strong passwords, regularly updating WordPress, plugins and themes, choosing secure web hosting and implementing security measures such as firewalls and two-factor authentication. Continuous education on security best practices and awareness of the latest threats are also essential.
To summarize, WordPress site security is an ongoing commitment. By being proactive and having a comprehensive security plan in place, you can protect your website and ensure a safe environment for yourself and your users.
